← information security policy meaning 42 information security policy templates [cyber security] ᐅ templatelab what is information security policy Information security policies: why they are important to your organization →
If you are looking for Information Security Policies: 10 Examples, Features, and Benefits | Syteca you've visit to the right web. We have 35 Pictures about Information Security Policies: 10 Examples, Features, and Benefits | Syteca like What is an Information Security Policy and Why is it Important?, What is an Information Security Policy and Why is it Important? and also Information Security Policies: 10 Examples, Features, and Benefits | Syteca. Here it is:
Information Security Policies: 10 Examples, Features, And Benefits | Syteca
 www.syteca.com
www.syteca.com
Information Security
 fity.club
fity.club
PPT - Session 3 – Information Security Policies PowerPoint Presentation
 www.slideserve.com
www.slideserve.com
security information policy policies session ppt powerpoint presentation support
III. Guidelines For Information Security Policy
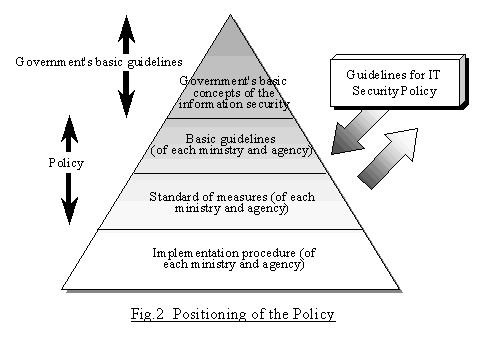 japan.kantei.go.jp
japan.kantei.go.jp
security policy procedure structure information japan guidelines setting up fig2 kantei 2001 jp go
10 Information Security Policies Organizations Should Implement
 www.ekransystem.com
www.ekransystem.com
IT Security Policy: Key Components & Best Practices For Every Business
 www.bmc.com
www.bmc.com
practices
PPT - Session 3 – Information Security Policies PowerPoint Presentation
 www.slideserve.com
www.slideserve.com
security information policies session policy ppt powerpoint presentation
PPT - Information Security Policy PowerPoint Presentation, Free
 www.slideserve.com
www.slideserve.com
10 Most Important Elements Of Information Security Policy - Sprinto
 sprinto.com
sprinto.com
Information Security Policies: 10 Examples, Features, And Benefits | Syteca
What Is An Information Security Policy And Why Is It Important?
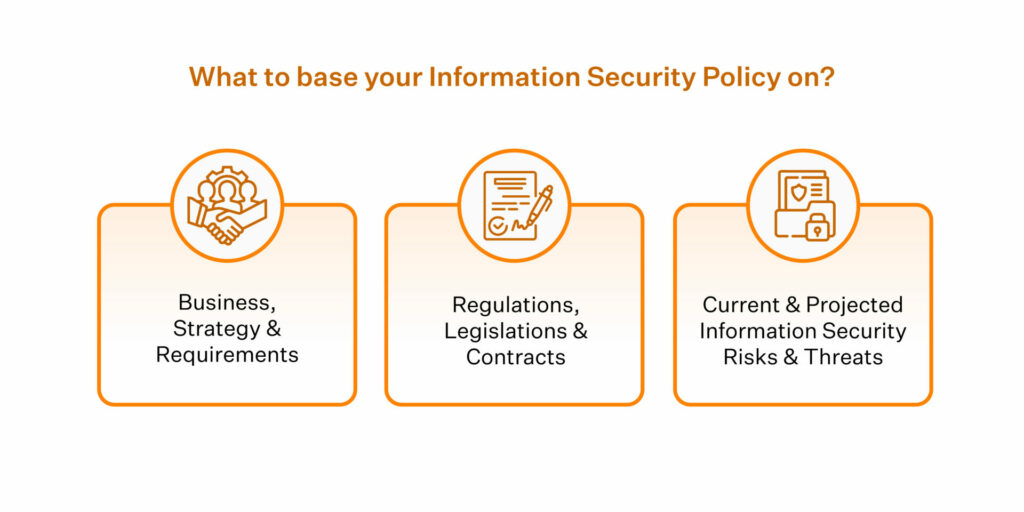 sprinto.com
sprinto.com
Types Of Security Policy | Bartleby
 www.bartleby.com
www.bartleby.com
Information Security Policy - Hampshire College
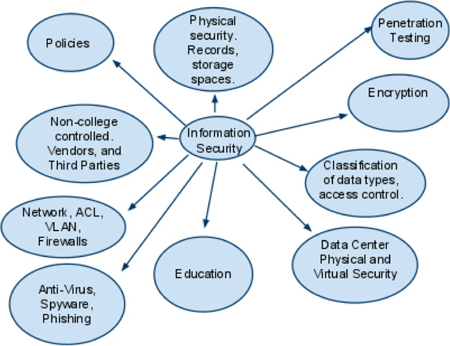 www.hampshire.edu
www.hampshire.edu
security policy information physical elements hampshire edu software training
Information Security Policy Decoded: A Extensive Guide
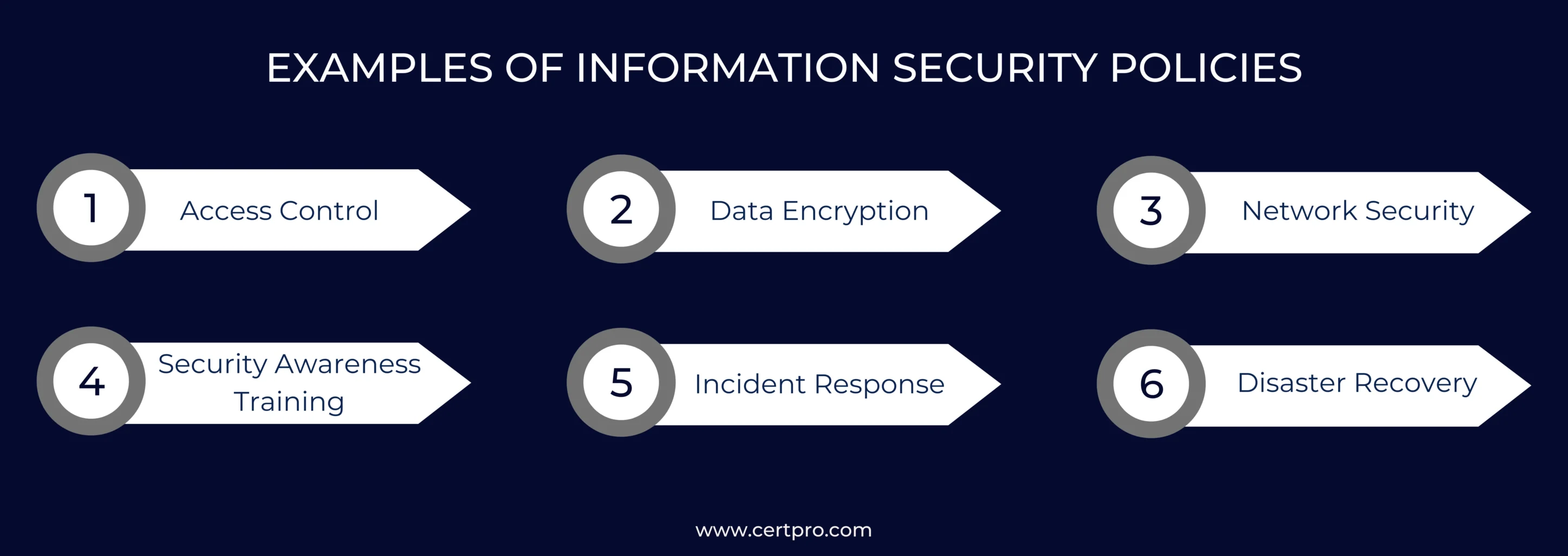 certpro.com
certpro.com
IT Security Policy: Definition, Types & How To Create One
 www.datamation.com
www.datamation.com
ISO 27001 Information Security Policy: A Quick Guide
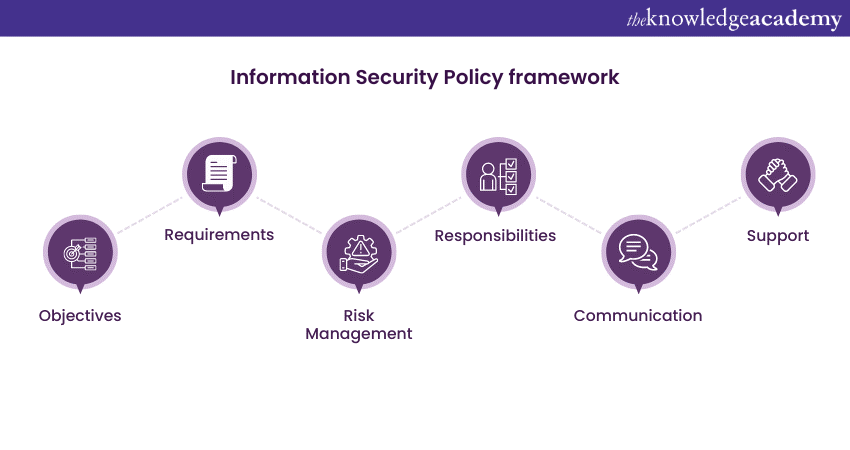 www.theknowledgeacademy.com
www.theknowledgeacademy.com
What Is The Purpose Of Defining A Framework For It Security Policies
 webframes.org
webframes.org
Information Security (InfoSec): Definition, Types, And Policy
 securitygladiators.com
securitygladiators.com
Security Policy Template - 13 Free Word, PDF Document Downloads
 www.template.net
www.template.net
security policy template information pdf document templates word business ac tees
What Is A Security Policy? Definition, Elements, And Examples (2022)
 kyloot.com
kyloot.com
Information Security Policies: 10 Examples, Features, And Benefits | Syteca
What Is An Information Security Policy? | UpGuard
 www.upguard.com
www.upguard.com
information
The Importance Of A Company Information Security Policy
 linfordco.com
linfordco.com
The Importance Of A Company Information Security Policy
 linfordco.com
linfordco.com
security policies importance auditor
Enterprise Information Security Policy: Definition & Components
 study.com
study.com
What Is An Information Security Policy And Why Is It Important?
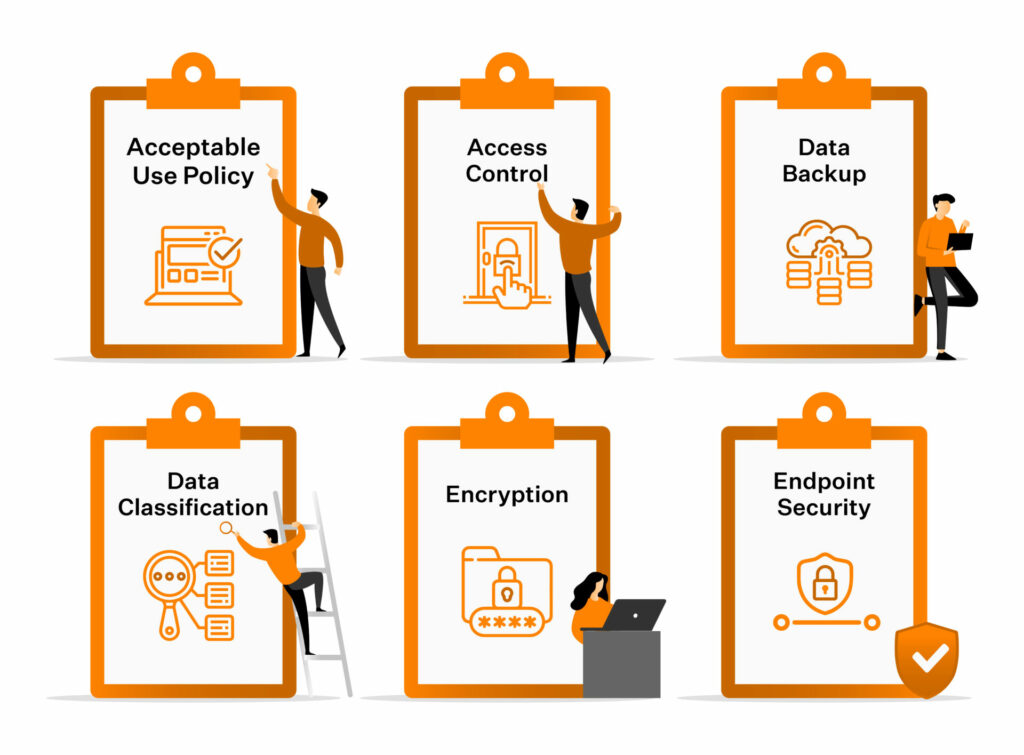 sprinto.com
sprinto.com
PPT - Session 3 – Information Security Policies PowerPoint Presentation
 www.slideserve.com
www.slideserve.com
security information policies policy session should ppt powerpoint presentation
13.Information Security Policy - YouTube
 www.youtube.com
www.youtube.com
policy security information
What Is A Security Policy? Definition And Its Components | The Global Hues
 theglobalhues.com
theglobalhues.com
What Is An Information Security Policy And Why Is It Important?
 sprinto.com
sprinto.com
The Key Elements Of An Effective Information Security Policy
 intone.com
intone.com
What Is An Information Security Policy And Why Is It Important?
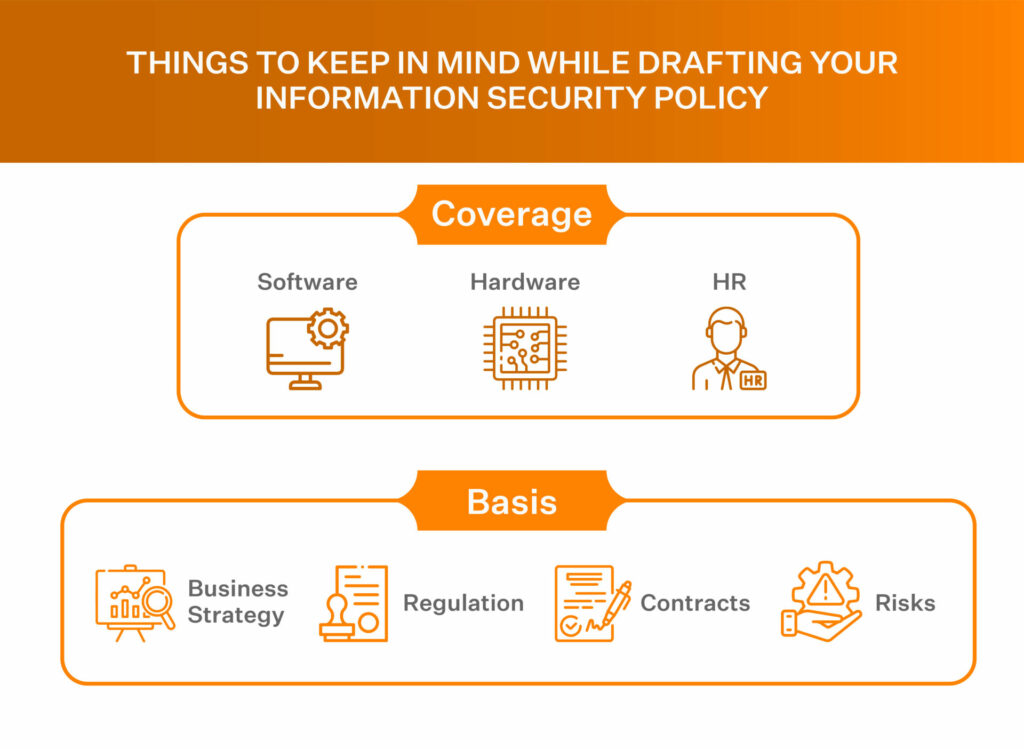 sprinto.com
sprinto.com
10 Most Important Elements Of Information Security Policy - Sprinto
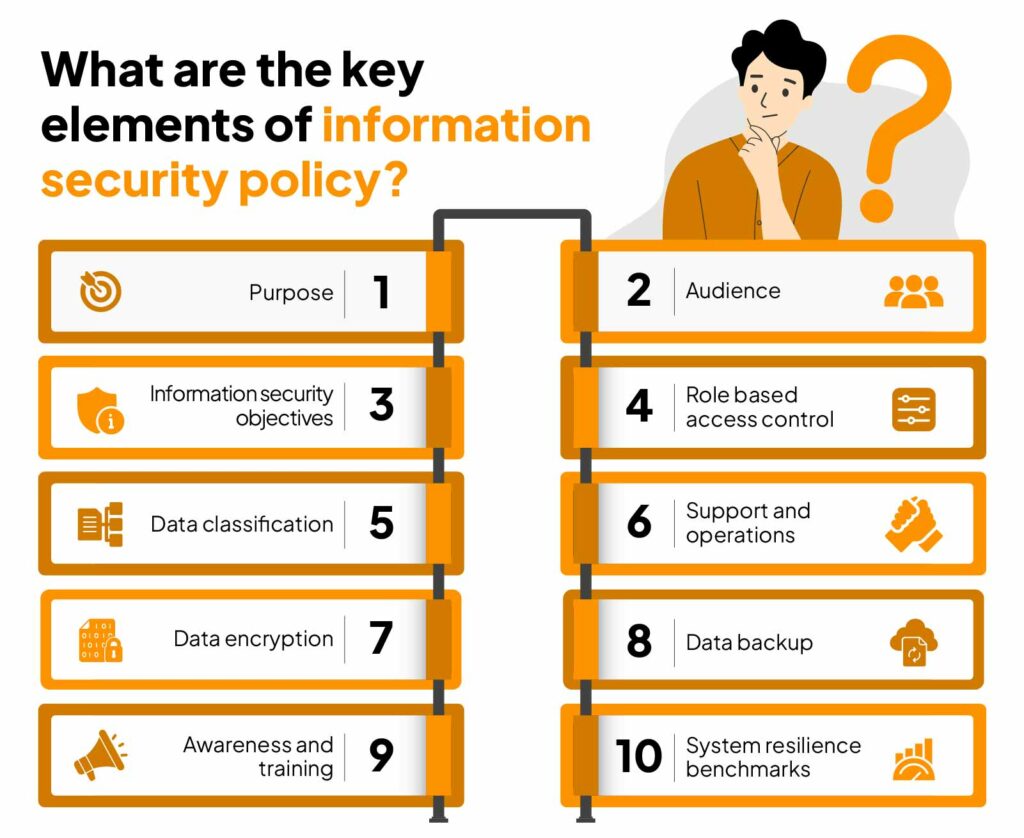 sprinto.com
sprinto.com
What Is An Information Security Policy And Why Is It Important?
 sprinto.com
sprinto.com
Develop And Deploy Security Policies | Info-Tech Research Group
 www.infotech.com
www.infotech.com
Security information policy policies session ppt powerpoint presentation support. Enterprise information security policy: definition & components. Iso 27001 information security policy: a quick guide